Hi,
Thanks for your question.
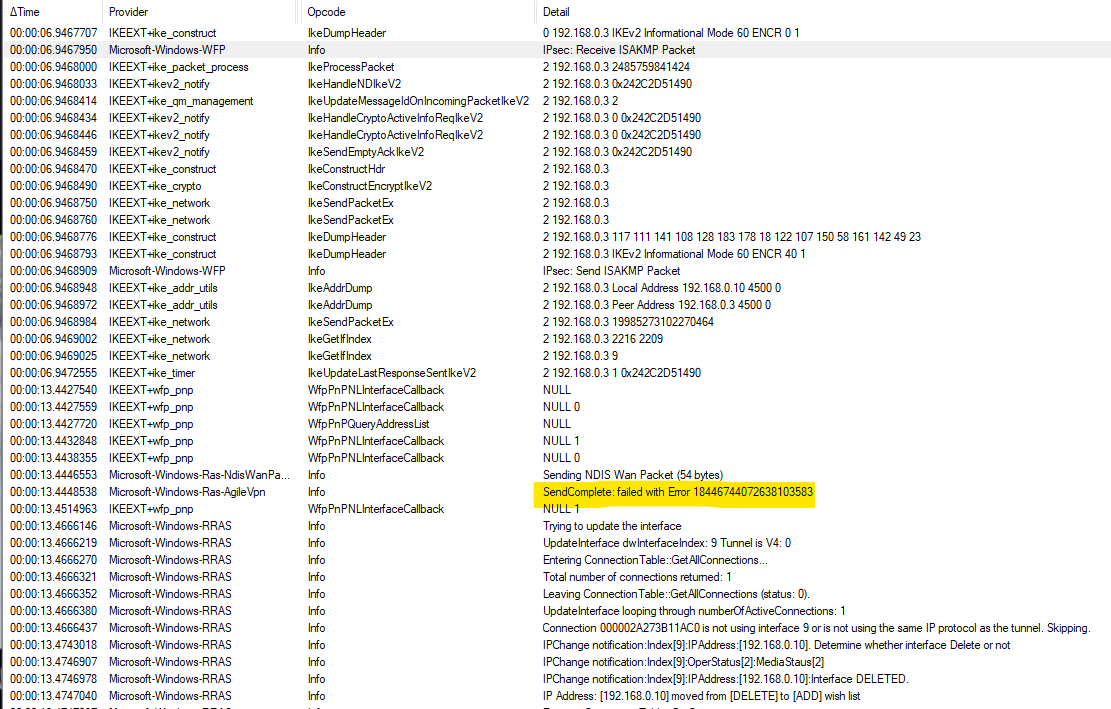
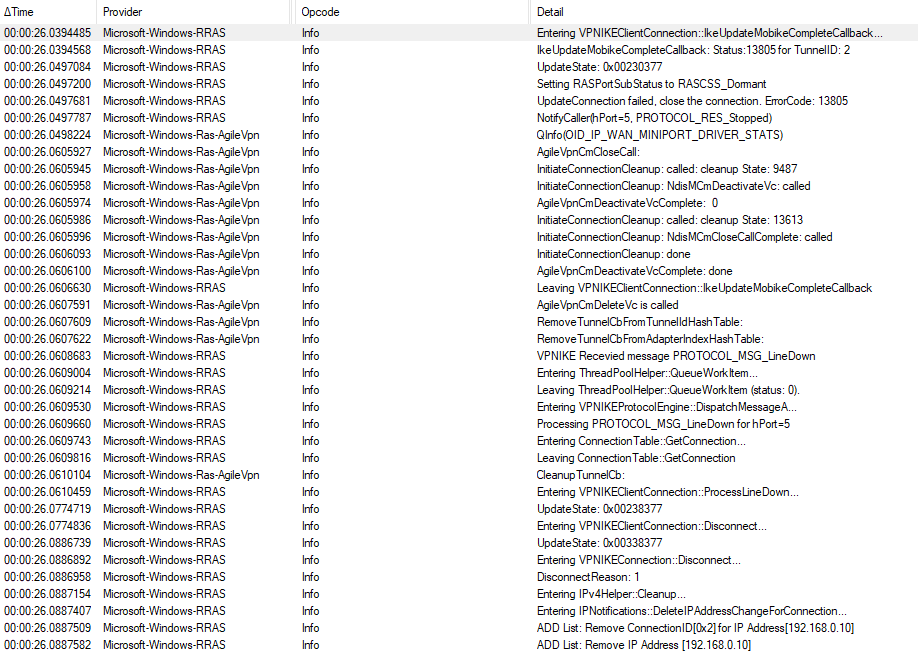
The error 829 appears when the modem (in the case of dial-up or broadband connections) or tunnel (in the case of VPN connections) is disconnected due to a network failure or a failure in the physical link to the modem.
The following are possible reasons for the failure.
1)A problem in the network between the modem and the RAS server might have caused the basic dial-up or, in the case of a broadband connection, PPPoE connection, or VPN tunnel to fail.
2)Please check connectivity between the modem and the telephone/cable connection jack. If an external modem is being used, check the physical connectivity between the modem and the computer.
3)In the case of VPN connections set up over a wireless network, problems in the wireless network might have caused the connection to fail. Check the status of the wireless connection in Network Connections folder.
Some of the causes of problems in the wireless network are:
The wireless access point might have gone down due to loss of power or for other reasons.
The user's computer might be out of the operating range of the wireless network or the RF signal strength might be weak.
4)The RAS server might have failed or restarted and closed the connection. Check the event logs on the RAS server.
5) Please also check the event viewer both on the VPN server and the problematic client if there’s any error event so that we can find more clue about this issue.
For more details, please refer to the following article.
Event ID 20226 — RAS Connection Termination
Best Regards,
Sunny
If the Answer is helpful, please click "Accept Answer" and upvote it.
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.